Why “Break-Fix” Works Entirely In The
Consultant’s Favor, Not Yours

Strengthen Your Business Security with Multi-Factor Authentication
In an age where cyber threats grow more sophisticated by the day, protecting sensitive business data is more critical than ever. Passwords alone are no longer enough to fend off modern cyberattacks. That’s where Multi-Factor Authentication (MFA) comes in—a powerful tool that adds an extra layer of security to your business systems.

Preparing for the Unexpected: The Importance of Incident Response Planning
Preparing for the Unexpected The Importance of Incident Response PlanningEven the most secure systems can face breaches, and when the unexpected happens, having a solid incident response plan can make all the difference. At TeleComp, we specialize in helping...

The Hidden Cost of Slow Internet (And What You Can Do About It)
Slow internet isn’t just frustrating. It quietly chips away at your business’s productivity, customer experience, and even employee morale. While it might seem like a minor inconvenience, underperforming connectivity can cost more than you think.

TeleComp’s Warren Balcom to Speak at National Automotive Conference
TeleComp is proud to announce that Warren Balcom, Director of Cybersecurity, Risk & Compliance, will present at the Automotive Parts Services Group National Conference this week in National Harbor, Maryland.
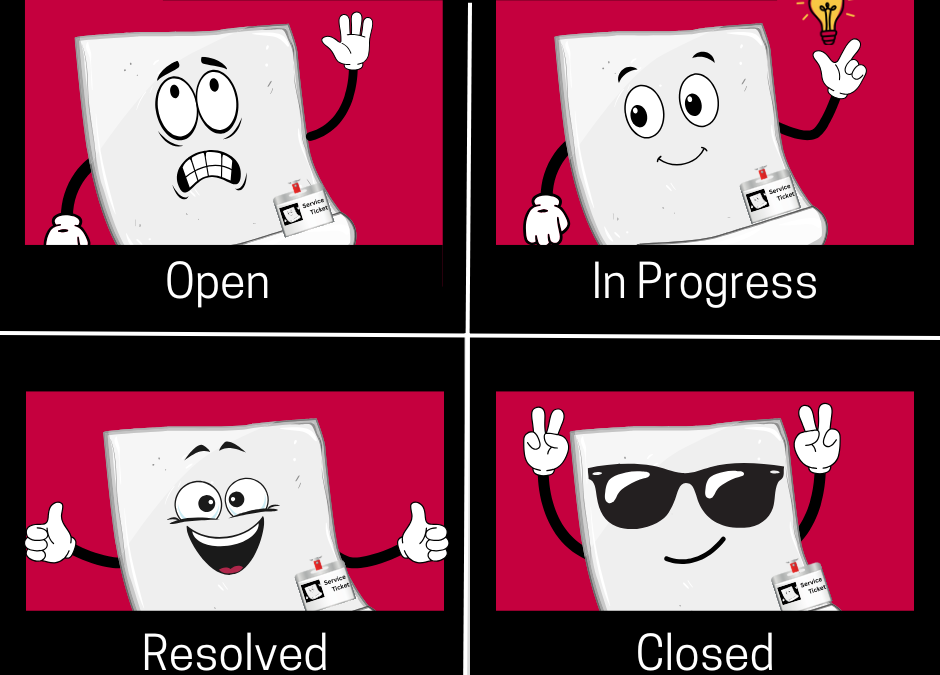
The Lifecycle of a Support Ticket
When an I.T. issue disrupts your workday, every minute counts. The way your technology partner handles support tickets can make a big difference. The Telecomp team understands that behind every ticket is a person depending on us to keep their business up and running. Here’s what actually happens when you submit a support request and what sets our process apart.

What Is Digital Equity and Why Your Business Should Care?
Digital equity isn’t just a buzzword. When communities have unequal access to the internet and digital tools, it creates gaps in education, employment, healthcare, and economic growth. But here’s the part that’s often overlooked: businesses are directly impacted by lower quality internet connectivity in the communities they serve.

Emerging Cybersecurity Threats Every Business Should Know About
Emerging Cybersecurity Threats Every Business Should Know About Cyberattacks targeting small businesses are increasing every year, and 2025 is expected to see even more sophisticated threats. From ransomware to phishing, small and medium-sized businesses (SMBs) are...

Navigating the Complexities of IT Compliance: A Step-by-Step Guide
Increasingly, businesses must navigate a growing web of IT compliance requirements to protect sensitive data, ensure privacy, and avoid hefty fines. With regulations such as GDPR, HIPAA, and CCPA constantly evolving, staying compliant can be challenging, especially...

TeleComp Expands Texas Presence with Dedicated Austin Team
TeleComp, a leading provider of managed IT, cybersecurity, business phone systems, and internet solutions, is expanding its Texas presence with a new dedicated team supporting businesses across the Austin-to-Houston corridor.

The Future of Work: IT Solutions for a Hybrid Workforce
The Future of Work: IT Solutions for a Hybrid WorkforceThe shift to hybrid work isn’t slowing down. As businesses adapt to a model that blends remote and in-office collaboration, IT solutions are playing a critical role in keeping teams connected, secure, and...
(January 15, 2022) Two schools of thought for managed IT – which are you?
A question I often get is “Why do I need to be on a managed IT plan? Can’t I just pay you to come out and fix things when they’re broken?” While that’s a legitimate question if we were talking about your washing machine or car, that’s definitely not the right approach to a critical and dynamic IT system that your company depends on; you definitely don’t want to wait until something “breaks” before you try and fix a problem. One virus or hacker attack or one slip-up can cause permanent data loss, extended downtime, a violation of data-breach laws, bad PR, loss of customers and sales, and a host of other expensive problems.
Additionally, under a “break-fix” model, there is a fundamental conflict of interests between you and your IT firm. The IT services company has no incentive to stabilize your computer network or to resolve problems quickly because they are getting paid by the hour; therefore the risk of unforeseen circumstances, scope creep, learning-curve inefficiencies, and outright incompetence are all shifted to you, the customer. Essentially, the more problems you have, the more they profit, which is precisely what you don’t want.
Under this model, the IT consultant can take the liberty of assigning a junior (lower-paid), technician, to work on your problem who may take two to three times longer to resolve an issue than a more senior (and more expensive) technician may have taken to resolve it. There is no incentive to properly manage the time of that technician or their efficiency, and there is every reason for them to prolong the project and to find more problems than solutions. Of course, if they’re ethical and want to keep you as a client, they should be doing everything possible to resolve your problems quickly and efficiently; however, that’s akin to putting a German shepherd in charge of watching over the plate of BBQ. Not a good idea.
Second, it creates a management problem for you, the customer, who now has to keep track of the hours they’ve worked to make sure you aren’t getting overbilled; and since you often have no way of really knowing if they’ve worked the hours they say they have, it creates a situation where you really, truly need to be able to trust they are being 100% ethical and honest and tracking their hours properly (not all do). And finally, it makes budgeting for IT projects and expenses a nightmare since your IT bill may be zero one month and thousands the next.
Plus, IT systems need regular monitoring and maintenance to protect against the 80,000+ brand-new malware attacks that are released every day, not to mention accidental hiccups in data backup, employee error, hardware failure, sabotage from disgruntled employees, etc. The list is long. So, if keeping your IT systems up and running is important to you – as is keeping your network secure from data loss and cybercriminals – then the only option you should choose is a “managed services” plan from a competent, trustworthy, and reliable IT services firm.
Related News

TeleComp Expands Texas Presence with Dedicated Austin Team
FOR IMMEDIATE RELEASE TeleComp Expands Texas Presence with Dedicated Austin Team Austin, TX — February 25, 2025 — TeleComp, a leading provider of managed IT, cybersecurity, business phone systems, and internet solutions, is expanding its Texas presence with a new...


