TeleComp Blog

Preparing for the Unexpected: The Importance of Incident Response Planning
Preparing for the Unexpected The Importance of Incident Response PlanningEven the most secure systems can face breaches, and when the unexpected happens, having a solid incident response plan can make all the difference. At TeleComp, we specialize in helping...

The Hidden Cost of Slow Internet (And What You Can Do About It)
Slow internet isn’t just frustrating. It quietly chips away at your business’s productivity, customer experience, and even employee morale. While it might seem like a minor inconvenience, underperforming connectivity can cost more than you think.
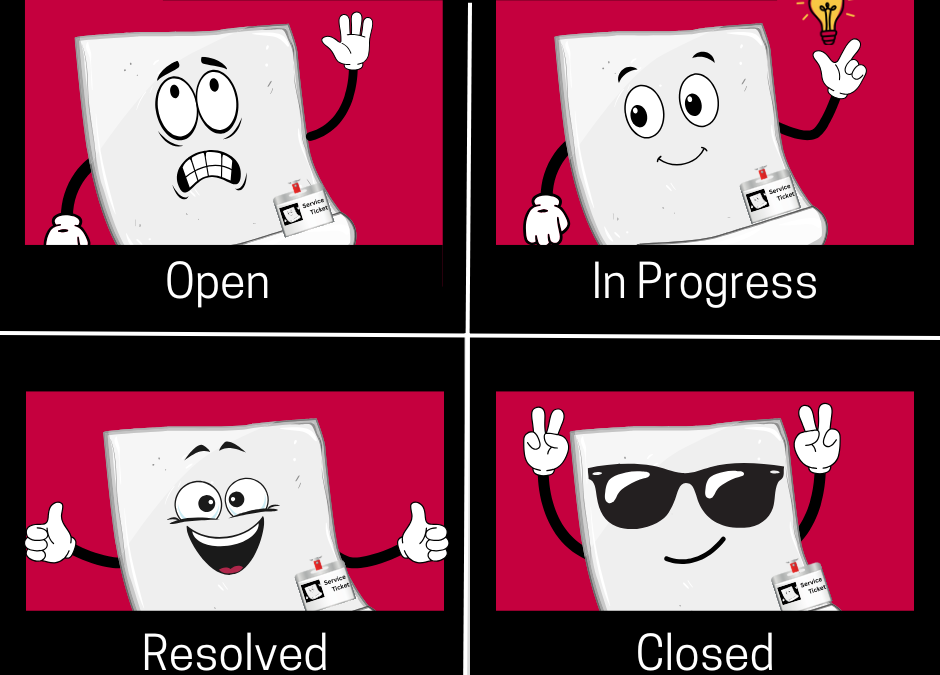
The Lifecycle of a Support Ticket
When an I.T. issue disrupts your workday, every minute counts. The way your technology partner handles support tickets can make a big difference. The Telecomp team understands that behind every ticket is a person depending on us to keep their business up and running. Here’s what actually happens when you submit a support request and what sets our process apart.

What Is Digital Equity and Why Your Business Should Care?
Digital equity isn’t just a buzzword. When communities have unequal access to the internet and digital tools, it creates gaps in education, employment, healthcare, and economic growth. But here’s the part that’s often overlooked: businesses are directly impacted by lower quality internet connectivity in the communities they serve.

Emerging Cybersecurity Threats Every Business Should Know About
Emerging Cybersecurity Threats Every Business Should Know About Cyberattacks targeting small businesses are increasing every year, and 2025 is expected to see even more sophisticated threats. From ransomware to phishing, small and medium-sized businesses (SMBs) are...

Navigating the Complexities of IT Compliance: A Step-by-Step Guide
Increasingly, businesses must navigate a growing web of IT compliance requirements to protect sensitive data, ensure privacy, and avoid hefty fines. With regulations such as GDPR, HIPAA, and CCPA constantly evolving, staying compliant can be challenging, especially...

The Future of Work: IT Solutions for a Hybrid Workforce
The Future of Work: IT Solutions for a Hybrid WorkforceThe shift to hybrid work isn’t slowing down. As businesses adapt to a model that blends remote and in-office collaboration, IT solutions are playing a critical role in keeping teams connected, secure, and...

The Costs of a Data Breach: How to Protect Your Business
The Costs of a Data Breach: How to Protect Your BusinessA data breach can cripple a business in more ways than one. From financial losses to reputational damage, the fallout can take years to recover from—if the business survives at all. In 2025, as cyberattacks grow...

What to Look for in an IT Managed Services Provider
What to Look for in an IT Managed Services ProviderChoosing the right IT Managed Services Provider (MSP) can be a game-changer for businesses looking to streamline operations, improve cybersecurity, and reduce downtime. As businesses rely more heavily on digital...
